Apache Security Configurations
In this tutorial, we will demonstrate how to set up additional security configurations for your PHP application hosted on an Apache application server.
There are two main methods to configure security settings:
- Modify the main configuration file of Apache (httpd.conf).
- Create a special .htaccess file, which contains one or more configuration directives and is placed inside your application directory.
The directives in the .htaccess file can override a subset of the server’s global configuration for that directory and all its subdirectories. The directives you can include in this file are determined by the AllowOverride directive.
AllowOverride is valid only in <Directory> sections specified without regular expressions. When this directive is set to None, .htaccess files are completely disregarded. When this directive is set to All, any directive that has the .htaccess context is allowed in .htaccess files.
Let’s examine the various types of security configurations you can apply to protect your application:
Each of these security configurations plays a crucial role in safeguarding your PHP application from potential threats and unauthorized access.
Setting Up the Authentication Request
To set up authentication for your Apache application or to secure a specific directory within your application, follow these steps:
- Generate a hash from your password: Use any htpasswd tool or an online service (for example, Web2Generators htpasswd generator).
- Create a simple text file containing the previously generated hash.
- Click the Config button for your server.
- Upload the created file to the /var/www/webroot/ROOT directory.
- Open the httpd.conf file (or .htaccess file, if you use it) located in the /etc/httpd/conf folder, and perform the following configurations:
To set up authentication for the entire application, add the following lines to the <Directory> section:
<Directory "/path/to/your/application">
AuthName "Restricted Area"
AuthType Basic
AuthBasicProvider file
AuthUserFile /var/www/webroot/ROOT/.htpasswd
Require valid-user
</Directory>These directives will enable basic authentication for your application, prompting users to enter a valid username and password to gain access. Adjust the path in AuthUserFile to match the location of your uploaded password file.
To set up authentication for a specific directory within your Apache application, add the following `<Location>` block, specifying the path to the required directory:
apache
<Location /directory_path>
AuthName "Restricted area"
AuthType Basic
AuthBasicProvider file
AuthUserFile /var/www/webroot/ROOT/.htpasswd
Require valid-user
</Location>Remember to save the changes and Restart the Apache server to implement the new configuration.
As a result, when accessing the application or the protected directory, the user will be prompted to authenticate.
Security Through Setting Up Criteria
You can secure your application by controlling access to specific parts of your server based on criteria such as client hostname or IP address.
The necessary configurations can be applied using the Require directive. To set up more complex access policies, you can use it in conjunction with:
- RequireAll: A set of authorization directives where none must fail and at least one must succeed.
- RequireAny: This directive represents a set of authorization directives where at least one must succeed.
- RequireNone: This directive represents a set of authorization directives where none must succeed.
To implement these configurations, navigate to the /etc/httpd/conf folder and open the httpd.conf file (or the .htaccess file directly in the target directory).
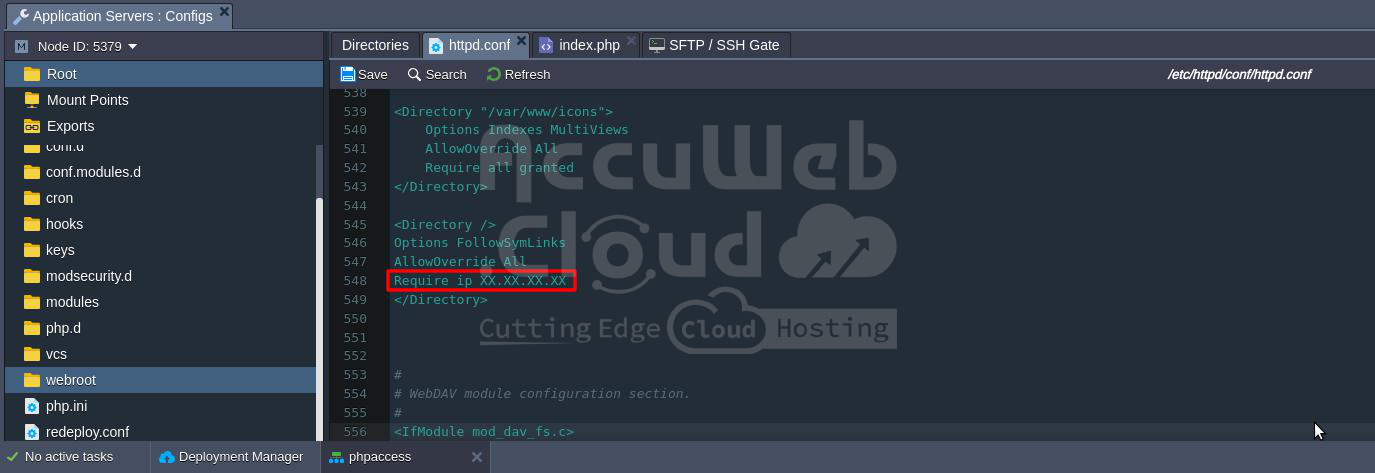
1. To set up access criteria by IP, simply add the necessary directive to the <Directory> section.
2. For a more complex example, you can configure an access policy with several conditions using the RequireAll directive for a specific server folder. Just modify the appropriate section as shown below:
3. Don’t forget to save the changes and Restart your Apache server to apply them.
Configuring mod_security Module
Mod_security is a really useful Apache module that adds a bunch of cool features. It can do things like filtering out bad stuff, checking URLs and Unicode encoding, keeping track of what’s going on (auditing), stopping sneaky null byte attacks, limiting how much memory uploads can use, hiding the server’s identity, and even creating a little secure bubble for it to run in. And that’s just the beginning!
By default, this module is pre-installed on the platform and can be configured using the /etc/httpd/conf.d/mod_security.conf file.
In this file, you have the flexibility to modify default configurations or add your custom settings. For example, you can incorporate additional ModSecurity Rules by uploading them to the /etc/httpd/modsecurity.d folder (e.g., modsecurity_crs_11_brute_force.conf).
Any rules uploaded to the modsecurity.d or activated_rules folders will automatically be activated without requiring additional settings. This is configured by default parameters in the /etc/httpd/conf.d/mod_security.conf file.
Include modsecurity.d/*.conf
Include modsecurity.d/activated_rules/*.confHide Apache Server Version
By default, Apache tends to show its version publicly, which can be risky as attackers may use this information to target vulnerabilities specific to that version or operating system. To mitigate this, the platform automatically incorporates the following configurations into your httpd.conf file:
To mitigate this, the platform automatically incorporates the following configurations into your httpd.conf file:
ServerSignature Off: This setting shows a 404 page instead of directory listings or other pages generated by Apache, which helps conceal information about the server.
ServerTokens Prod: This setting determines the HTTP response header for the Apache Server. With the value set to “Prod,” the HTTP response header will appear as follows: “Server: Apache,” providing minimal information to potential attackers.