Traefik V2 Ingress Controller in AccuWeb.Cloud Kubernetes Service
When deploying applications in Kubernetes, an Ingress Controller plays a crucial role in managing external access to services. At AccuWeb.Cloud, you can choose from popular ingress controllers like NGINX, Traefik, or HAProxy.
In this blog, we’ll dive into Traefik v2, the modern version of Traefik, and explore its updates and advantages in the AccuWeb.Cloud Kubernetes Service (AK8s).

Why Traefik for Kubernetes?
Traefik is a cloud-native reverse proxy and load balancer designed to integrate seamlessly with containerized environments. It automatically discovers services, handles routing, and provides advanced features like:
- Automatic HTTPS (via Let’s Encrypt)
- Dynamic service discovery
- Native Kubernetes CRD support
- Load balancing and sticky sessions
- Metrics and observability integration (Prometheus, Grafana)
This makes Traefik a perfect fit for modern microservices and cloud-native apps.
No Frontends and Backends
The basic concepts of frontend and backend have changed to routers, services, and middleware in Traefik v2.
In Traefik v1, the router replaces the frontend, and the service replaces the backend, with each router connected to a service.
In Traefik v2, middleware pieces are added to routers to adjust requests before they reach the services. These middleware pieces can be linked together to handle different scenarios, and any router can connect to any middleware instance.
Middleware
There are many types of middleware available. In addition to handling traditional HTTP requests, different middleware can modify request parameters and HTTP headers, manage redirects, add authentication, and more.
The middleware attached to a router can modify a request before it is sent to the service.
Here are some examples of middleware used in request routing:
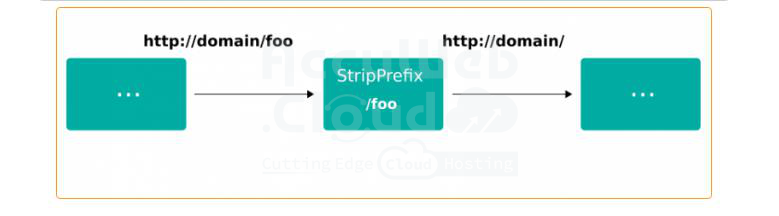
- stripPrefix: Removes a prefix from the path. Use this if your backend serves the path “/”, but needs to be accessed with a specific prefix, like “/foo”. This middleware replaces the frontend.rule.type annotation in Traefik v1.
http:
middlewares:
test-stripprefix:
stripPrefix:
prefixes:
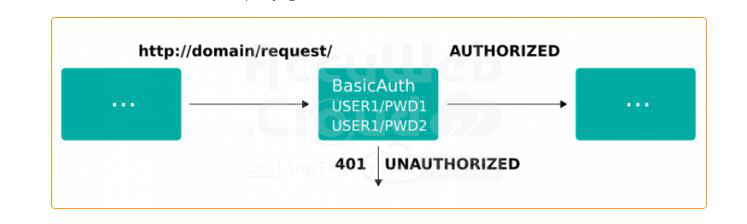
- "/foo"- basicAuth middleware is used to set up basic authorization. For example:
http:
middlewares:
test-auth:
basicAuth:
users:
- "user1:$apr1$Kveg6cv0$yJn5mwyfBy7luzZ9Fi1AH0"
- "user2:$apr1$w70ASLDx$1UJmrFL/lVoltjmAz4UDH/"This middleware is an alternative to using Kubernetes Secrets for credentials and restricts access to services.
It replaces the Traefik v1 annotation.
traefik.ingress.kubernetes.io/auth-type: "basic".Using Multiple Middlewares
Using middleware (and other routing components) is optional. You can use multiple middleware or none at all. For example, in the Ingress below, one middleware handles authentication, and another removes a source path prefix.
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: monitoring-prometheus-alertmanager
namespace: kubernetes-monitoring
annotations:
kubernetes.io/ingress.class: traefik
traefik.ingress.kubernetes.io/router.middlewares:
kubernetes-monitoring-alert-auth@kubernetescrd,
kubernetes-monitoring-alert-prefix@kubernetescrd
spec:
rules:
- http:
paths:
- path: /prometheus-alert
pathType: Prefix
backend:
service:
name: monitoring-prometheus-alertmanager
port:
number: 80
---
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: alert-auth
namespace: kubernetes-monitoring
spec:
basicAuth:
secret: monitoring-prometheus
---
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: alert-prefix
namespace: kubernetes-monitoring
spec:
stripPrefix:
prefixes:
- /prometheus-alertProviders
Traefik v2 introduces the concept of a provider, which supplies routing information to Traefik. When Traefik detects changes, it automatically updates the routes. The Kubernetes Ingress Traefik provider offers traditional Kubernetes ingress controller functionality.
In addition to the standard Ingress, Accuweb.cloud KS now supports IngressRoute, a Custom Resource Definition (CRD) for a Traefik HTTP router. This makes it easier to access K8s clusters without needing annotations. You can see an example of how to use IngressRoute in our K8s repository.
Services
Traefik v2 includes specific Services that configure how to reach the actual Kubernetes services that handle incoming requests.
http:
services:
my-service:
loadBalancer:
servers:
- url: "http://<private-ip-server-1>:<private-port-server-1>/"
- url: "http://<private-ip-server-2>:<private-port-server-2>/"Traefik also includes a variety of internal services. For example, in the config file found in the AccuWeb.Cloud KS repository, there’s access to a built-in Traefik v2 dashboard service via IngressRoute.
These are just a few of the main changes in the new Traefik v2 version implemented in AccuWeb.Cloud Kubernetes v1.21.2+. You can find a complete list of changes in the official documentation detailing the transition from Traefik v1 to v2.
Start using Kubernetes Service, which can be automatically deployed, scaled, and updated using AccuWeb.Cloud dashboard. Keep an eye out for new releases as well.
People Also Ask (And You Should Too!)
1. What is an Ingress Controller in Kubernetes?
An Ingress Controller is a Kubernetes component that manages external access to services within a cluster, typically HTTP and HTTPS traffic. It routes requests from outside the cluster to the correct internal services.
2. Why use Traefik as an Ingress Controller?
Traefik is lightweight, cloud-native, and integrates seamlessly with Kubernetes. It provides features like automatic SSL certificate management, dynamic configuration updates, traffic routing, and monitoring dashboards, making it a popular choice over traditional ingress controllers.
3. What’s the difference between Traefik v1 and v2?
- Traefik v1: Used static rules, simpler but less flexible.
- Traefik v2: Introduces CRDs (Custom Resource Definitions) like IngressRoute, better routing capabilities, improved middlewares, and enhanced observability. It is more powerful and customizable for production workloads.
4. Does AccuWeb.Cloud Kubernetes support both Traefik v1 and v2?
Yes. Older Kubernetes versions on AccuWeb.Cloud support Traefik v1. Starting from Kubernetes version 1.21.2 and above, Traefik v2 is the default ingress controller.
5. Can I switch from NGINX to Traefik on AccuWeb.Cloud?
Yes. AccuWeb.Cloud Kubernetes clusters let you choose between NGINX, Traefik, or HAProxy ingress controllers. You can select Traefik during cluster setup or reconfigure an existing cluster.
6. Is Traefik v2 suitable for production workloads?
Absolutely. Traefik v2 is designed for scalability, security, and high availability. It supports load balancing, retries, circuit breakers, and TLS termination, making it production-ready.
7. How does Traefik handle SSL/TLS certificates?
Traefik v2 has built-in support for Let’s Encrypt. It can automatically issue and renew SSL certificates for your services, ensuring secure HTTPS traffic without manual intervention.
8. Can Traefik v2 integrate with monitoring tools?
Yes. Traefik v2 offers metrics for Prometheus and supports logging integrations. This makes it easy to monitor performance, detect anomalies, and optimize traffic routing.
9. When should I use Traefik instead of NGINX in Kubernetes?
Choose Traefik if you need:
- Dynamic, cloud-native routing
- Automated SSL certificate management
- Better middleware support (rate limiting, authentication, etc.)
- Modern architecture for microservices

Jilesh Patadiya, the visionary Founder and Chief Technology Officer (CTO) behind AccuWeb.Cloud. Founder & CTO at AccuWebHosting.com. He shares his web hosting insights on the AccuWeb.Cloud blog. He mostly writes on the latest web hosting trends, WordPress, storage technologies, and Windows and Linux hosting platforms.